33 tips to stay safe online & keep hackers away
It’s impossible to watch the news these days without hearing about hackers breaking into another corporate database and making off with sensitive user login information and credit card details. It might feel to some people that the Internet is becoming a rather risky place to be, and it isn’t safe to do anything online. But as with the offline world, it’s simply a matter of taking precautions and using common sense. If you do that, you will stay safe online and enjoy the benefits that the internet has to offer.
Below, we have outlined a mighty 33 tips to stay safe online and minimize your risk of being hacked. Obviously, this is not going to help if a company you’re a customer with gets hacked. But by following these simple, straightforward tips, you can minimize your exposure and contain any damage.
Read more: What is a cybersecurity analyst?
QUICK ANSWER
Tips to stay safe online include using encrypted accounts, minimizing your personal information online, using malware trackers, and using stronger passwords. You should also be careful of clicking on email links and downloading files with certain file formats.
JUMP TO KEY SECTIONS
The various threats making it difficult to stay safe online
Let’s start with outlining some of the threats currently doing the rounds online today. Online scams and dangers come and go, and some evolve into something else entirely. But here are the common ones that stick around like a bad smell and make it difficult to stay safe online.
- Phishing (pronounced ‘fishing’) — this is when you’re sent an email made to look like it came from a trusted company (your bank, insurance company, employer, etc.). You are then told there is an issue with your account, and you need to sign in to ‘verify your details.’ Of course, they give you a handy sign-in link that goes straight to their website. How nice of them.
- The Nigerian Prince email — we’ve ALL had this one (or variations of it.) You’re informed that a certain someone died without leaving a will, and there’s $50 million sitting unclaimed in a bank. The person offers to cut you into the money in exchange for your bank account details.
- The romantic stranger — female friends of mine on social media are hit particularly hard by this one. The scammer sweet-talks the person and eventually tells them they love them. Then they make commitment promises and ask for money.
- Ransomware — this is becoming an increasingly common danger online for companies. A hacker will lock down a company’s entire database and refuse to release it unless a ransom is paid. If the victim refuses, the database is remotely erased. Even if the victim pays, there’s no guarantee the database won’t be erased anyway.
- Malware — the oldie but still alive and kicking. Planting viruses and malware on other people’s computers will always be an easy way to disrupt their lives.
- Identity theft — again, a very common one. The more information you leave online about yourself, the more you leave yourself open to identity theft.
Determining your risk level

Before you move on to the tips below, you have to calculate what your actual risk level is. This is called threat modeling.
By this, I mean that each person has a higher or lower chance of being attacked. For example, the President of the United States has an extremely high-risk level because of who they are and the conversations they are having with people on a daily basis. I, on the other hand, a writer with Android Authority, don’t have to worry about the Chinese government hacking into my phone conversations and hearing my pizza delivery order.
In other words, compared to the US President, I’m a rather boring guy. I have a completely different threat model compared to a world politician or a celebrity. You also have to decide where on the scale you fall based on certain criteria.
Do you fall into one of the following categories?

Here are some potential scenarios that could heighten your threat level and make it difficult to stay safe online.
- Do you have a vengeful ex-partner (romantic or business) who is out to get dirt on you?
- Do you have a stalker?
- Are you going through a messy divorce or child custody hearing?
- Are you a business owner with sensitive proprietary information that someone is likely to steal from you?
- Are you a controversial, polarizing person?
- Are you a public official or celebrity?
- Were you a witness to a crime and potentially in danger?
Factors like this can drive up your chance of being hacked online and make it less likely you will stay safe when on the internet. However, on the flip side of the coin, 99% of people are boring everyday folk who go to work, come home, watch TV, and go to bed. They have very little to fear from a hacker who will deem them a waste of time.
But that’s not to say you should let your guard down completely. The point is not to panic and blow things out of all proportion. Assess your possible weaknesses and tweak the following tips accordingly based on your individual needs.
33 tips to minimize your hacking risk and stay safe online
Let’s now go into the various ways you can tighten up your online security. Look upon this as a nice weekend project.
Use encrypted email

These days, everyone and their dog has a Gmail account. Everyone loves Gmail for its huge amount of storage space and cool features. However, from a privacy perspective, it’s a nightmare.
True, they have two-factor authentication, so getting into a 2FA-enabled Gmail account is extremely difficult. But any email and user metadata that hits US Google servers immediately fall under the jurisdiction of the US intelligence agencies, including the National Security Agency. In the UK, that would be MI5 and GCHQ. In fact, any country signed up to the Fourteen Eyes agreement routinely share information among themselves. Google complies with all requests to hand over whatever is demanded of them, so don’t expect them to put up any kind of a fight on your behalf.
Instead, use ProtonMail. This is an encrypted email service out of Switzerland, and the servers are in a heavily guarded data center inside a mountain, the location of which is a big secret. Switzerland’s extremely strict data privacy laws all but ensure that any requests by governments and law enforcement to hand over emails and user metadata will be politely rebuffed. Look upon it as the email equivalent of putting all your money in a Swiss bank account.
You can hook up a custom domain, and it will even import all your Gmail email, contacts, and calendar entries for you to ensure a smooth transition over. You can get a free account, but for serious email power users, you need to pay a small amount annually (which usually includes other Proton products bundled in.)
If you MUST use Gmail……

If you really can’t tear yourself away from Gmail, then consider encrypting your emails to stay safe online. It’s not foolproof by any means, and a determined intruder with means will finally crack it. But any casual opportunists will soon give up.
One option which I recently wrote about is FlowCrypt. It’s a Chrome extension that puts an encryption button on the Gmail interface and converts your message into PGP (Pretty Good Privacy). The person at the other end also needs FlowCrypt and can immediately decode the message.
Of course, another alternative is just to download your email to a local email client such as Outlook or macOS Mail. Then set your online email service to delete the copies on their server.
Use a disposable email address to sign up for mailing lists
If you decide to sign up for mailing lists, you really shouldn’t be using your main email address. If anyone is tracking you via your email, then they can see your tastes and proclivities based on what email newsletters you subscribe to. So for mailing lists, you have two options – convert the newsletter to an RSS feed (I know, old school) or use an anonymous email address (just set up another Protonmail address.)
You probably think that RSS is all but dead. It’s true that its usage is declining in the face of social media, but it’s still around. Sign up for an RSS reader service, then sign up for the email newsletter with Kill The Newsletter. It will generate a randomly-generated email address to sign up for the list and an RSS feed to access the newsletters when they come out.
Don’t click on any links inside emails
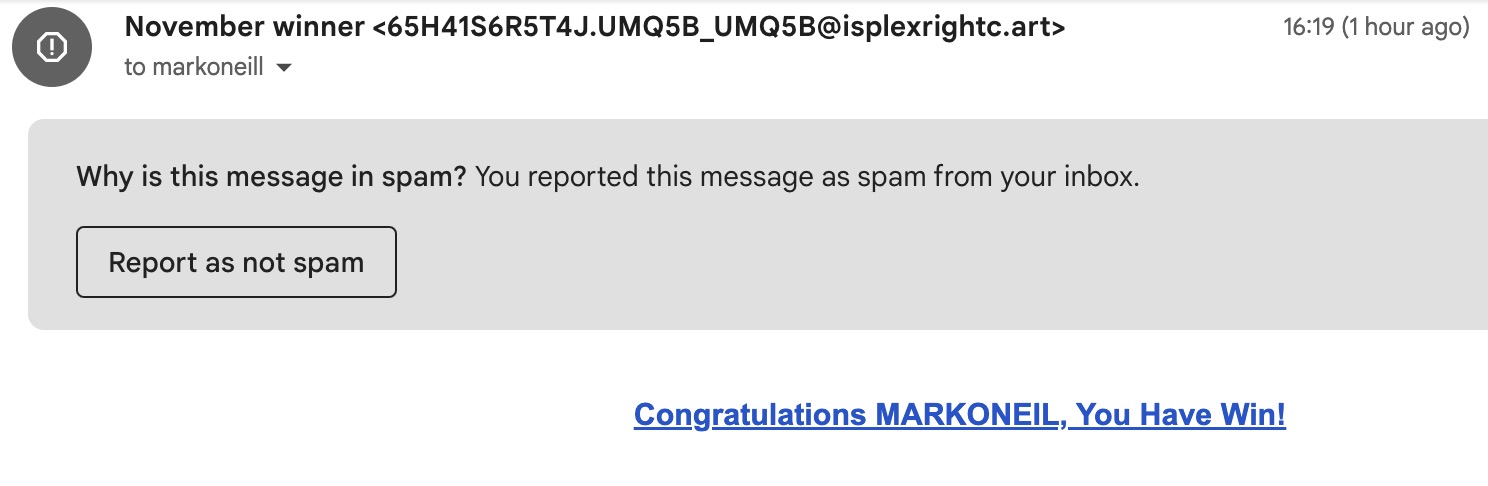
As we explained in a previous section, people who send phishing emails rely on you clicking a link in the email. This then sends you to a convincing-looking copy of an official website, one that they control. Once you enter your data into it, they’ve got you.
That’s why the golden rule to stay safe online should always be – never, ever click on any email links. Never. No exceptions. If you need to check the status of an online account, open your browser and manually type in the website address. Then log in yourself. Besides, any legitimate company would never ask you to click an email link to ‘verify your details’ for this precise reason.
Be wary of downloading email attachments
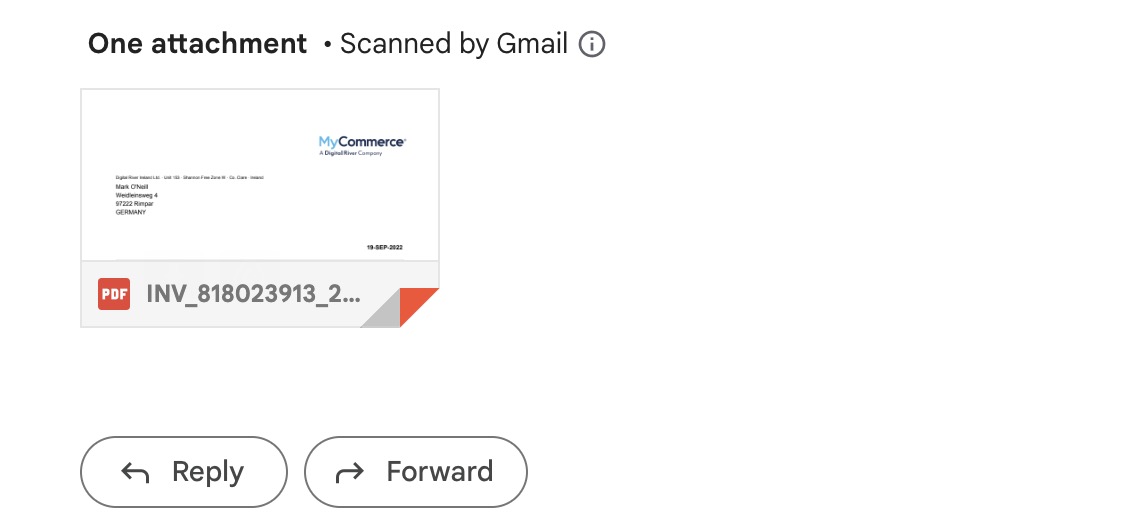
Email attachments are another way of passing on viruses and malware. Be extremely cautious of what you download. One good Gmail feature is that they virus-scan anything under 25MB in size. But if they can’t scan it, or the attachment looks suspicious in any way, either contact the sender via another communication method to ask about it or run the attachment through a virus scanner unopened, such as VirusTotal.
Switch to encrypted messaging
We’re big fans of WhatsApp here at Android Authority, but like Gmail, WhatsApp is a privacy minefield. Despite boasting of end-to-end encryption, they are sharing user metadata with their owners, Facebook. Yes, that Facebook. The one that will sell your data off the back of a lorry for a dollar. This is despite an earlier promise not to share that metadata. And if WhatsApp is not great for that reason, then it stands to reason that Facebook Messenger is just as bad, if not worse.
Apple devices are good when it comes to encryption, but don’t think for a moment that iMessage is a gift from the encryption Gods. Yes, iMessage is encrypted end-to-end, but iMessage history is synced with iCloud, which sits on Apple’s servers that can – and does – get handed over to law enforcement authorities. That encryption suddenly doesn’t look so good, does it?
The best alternative, by far, is Signal. No logs, no trackers, and no stored user information whatsoever, which means nothing to hand over to the law if they come knocking on Signal’s door. The encryption protocols are also top-notch, and the app is completely free and open source. You can also get a version for your computer and sync over the conversations.
Consider a more privacy-based browser such as Firefox, Brave, or Tor
Chrome is a good browser, but being a Google-owned property, it is as secure as Gmail. Forget Safari as well. Instead, consider a more privacy-based alternative such as Firefox, Brave, or even Tor.
Tor has a reputation for being the browser everyone goes to access the Dark Web. This is a slightly unfair blemish, as Tor does a lot of good as well to stay safe online. In countries with oppressive regimes, Tor can literally mean the difference between life and death. Human rights activists, bloggers, journalists, opposition politicians….the list of people who benefit from Tor every day is huge.
The problem with Tor, though, is that it is very slow, as it has to go through various proxy relays to ensure your privacy. So don’t try streaming any media through it. Plus, going anywhere near the Dark Web would not be a good idea.
Whichever browser you end up choosing, be sure to update it as soon as a new patch becomes available.
Don’t visit a website that doesn’t have a security certificate

These days, it’s standard Google policy to deprioritize any website without a security certificate. A website security certificate is when it starts with HTTPS and has a padlock next to the browser URL.
HTTPS ensures that there are no “man in the middle” attacks where sensitive user information has the potential to be intercepted. All big-name websites today use HTTPS, especially e-commerce websites and banking sites.
If a website you’re visiting only says HTTP, then it may be best to give it a wide berth. The site may not necessarily be bad on its own, but any information you put into that site will be insecure and wide open for the taking.
Keep your mobile apps up to date

This is a big one which a shocking number of people don’t bother with, in my experience. They look upon app updates as a pain in the neck and very inconvenient. But in reality, it’s the opposite. They’re there to protect your phone by plugging security vulnerabilities and bugs. So why shouldn’t you take advantage of them?
Remove your mobile number from online accounts

Edgar Cervantes / Android Authority
When it comes to an online attack from a hacker, the main point of weakness is arguably a mobile phone number. If you think about it, two-factor authentication codes can come as an SMS message. If a hacker knows your number, they can clone your SIM card and intercept those codes. People can impersonate you if they have a cloned phone with your number. They would also have access to your contacts with their information.
Therefore, try not to give out your mobile number to too many people. In fact, make it a policy to give it out extremely sparingly. Remove it from as many online accounts as possible to stay safe online. If a website or company demands a phone number, either give them a disposable prepaid SIM card or, even better, set up a VoIP number with either Skype or Google Voice.
Don’t sideload unsigned and unverified mobile apps
Joe Hindy / Android Authority
This may be a controversial one, especially with all you Android users. After all, sideloading is popular, even if it is insecure. But there is a reason why Google has security restrictions in place to discourage sideloading, and it isn’t to ruin your day.
For those unfamiliar with the terminology, sideloading is when you install a mobile app by transferring the APK file directly onto your device. It, therefore, bypasses the Play Store and its safeguards, so if that app has malware in it, it isn’t going to be detected. Play it safe and stick to tested and verified apps on the Play Store. Any security vulnerabilities will have been detected by Google and removed from the Play Store (you would hope, anyway.)
Use disposable digital debit cards
The old joke is that you can buy whatever you want if you look online. If you want that combined coathanger and cigarette lighter that plays German schlager music, then surely there’s a website that caters to your desires. But how do you know if you can trust that website store with your credit card details?
The answer is one-off disposable free digital debit cards. Transferwise, for example, offers digital card numbers that you can use for one-off purchases. Once the transaction has gone through, you can cancel the number for free, preventing anyone from reusing it. Then you can generate a new number for your next online purchase. Rinse and repeat. You can even put the card on Apple Pay or Google Pay to make it easier to pay at the online store. Ask your bank if they, too, offer virtual cards.
Build up an online persona
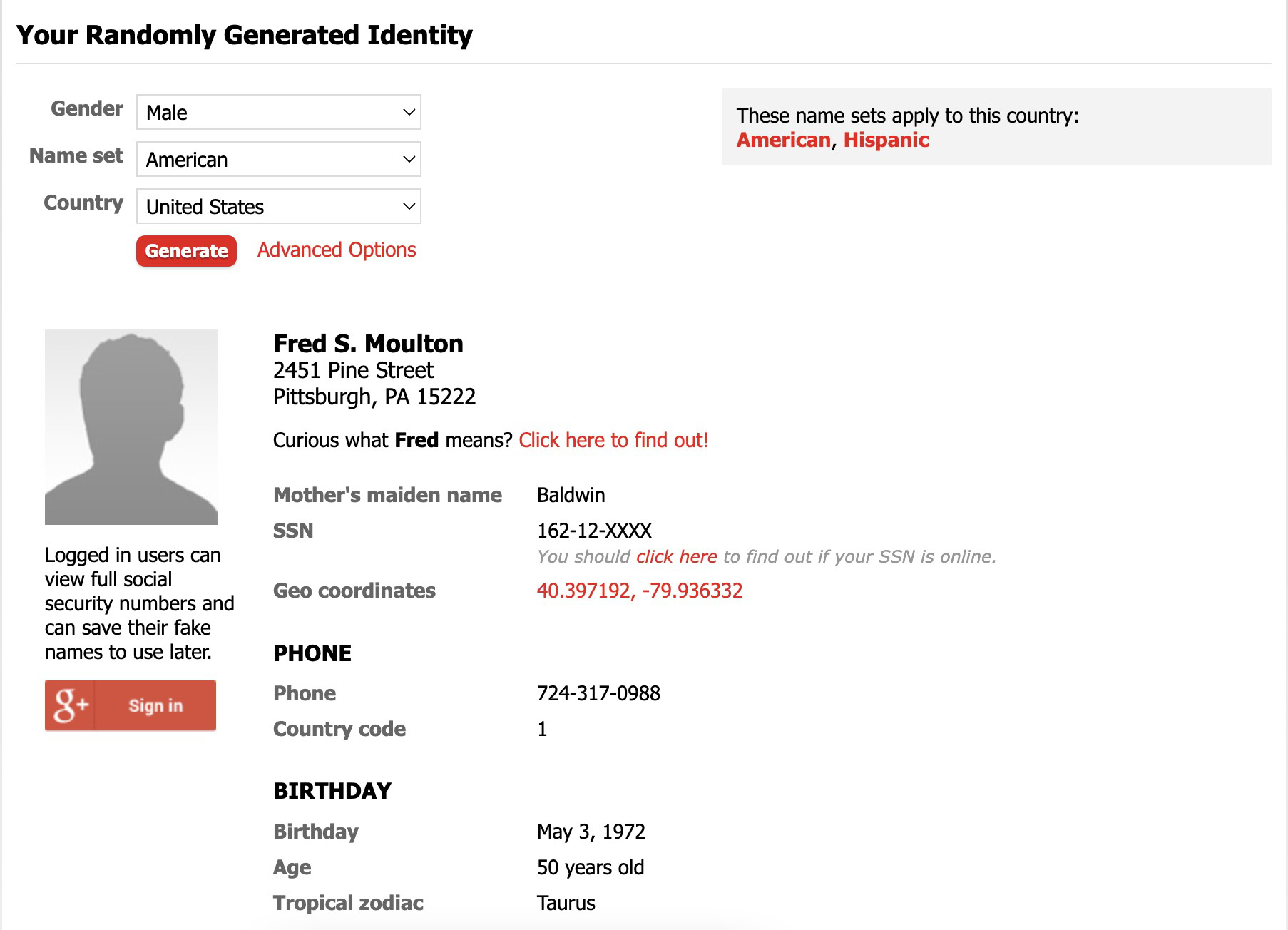
You’re going to think I am going all James Bond here with my fictional identity and backstory, but hear me out here. How many forms have you filled out that have asked for your name, address, phone number, date of birth, zip code, and other needless information? Information like this is what makes identity theft and data harvesting possible, so the last thing you should do is put in your real data if you want to stay safe online.
If you find it a drag to keep coming up with fake information, a handy website that randomly generates this information can make your life a lot easier. My go-to site is Fake Name Generator. Enter your gender, nationality, and country, and the site will spit out a new set of stats for you. Obviously, it goes without saying that you shouldn’t use fake information for legal documents and to commit a crime.
Download a password manager & improve your passwords

Joe Hindy / Android Authority
Calvin recently wrote a couple of great articles on password managers and why you should use one. The biggest weak point when it comes to online security has always been the password. Two-factor authentication made the login password much more secure, but that doesn’t mean you shouldn’t make a huge effort with your password. I wrote an article on this very subject not too long ago, and you really should read it.
Making passwords like $40lkHß#Wq3VByL@ has its drawbacks, though – it’s impossible to remember unless you have a photographic memory. We use LastPass here at Android Authority, but there are equally good alternatives, such as KeePass, 1Password, and Dashlane. In a pinch, you can use the password manager in your browser, but you shouldn’t if you share your computer with other people.
Use two-factor authentication
Along with a stonking big password, you should also enable two-factor authentication on every platform that supports it. These days, all the big players do – Google, Facebook, Reddit, Twitter, Instagram, iCloud, Dropbox, and more. If it’s there, use it. It can be a bit inconvenient to retrieve the extra code, but not as inconvenient as having your valuable account hijacked.

If you don’t want to use an authenticator app, you could get SMS messages with your code, but this is insecure. The best method to stay safe online, outside an authenticator app, is a Yubico hardware key that slots into a USB slot on your computer and uses your fingerprint to authenticate.
Use cloud storage platforms sparingly

Cloud storage platforms are very useful, and I admit to having accounts on nearly all of them. But they should only be used very sparingly, and sensitive documents should stay off them altogether. Should sensitive information really be kept on someone else’s server that you don’t control? Better to use a removable hard drive instead or a NAS drive.
There’s nothing wrong with using cloud storage to move files around between devices and to share files with other people. But try to make it a habit not to keep files on there long-term. Cloud storage has the potential to be hacked, just like any other online company.
Lock down your website login page

Edgar Cervantes / Android Authority
If you have your own website, and it runs WordPress, then you need to make sure it’s locked down tight. To date, I’ve had over 200,000 brute-force attempts to get into my website (over a seven-year period), so I’m very aware that having your own website is a very alluring target for bad actors online. This subject is a whole other article of its very own, but here are the brief highlights.
Use a VPN

If you say “VPN” to someone, they will most likely associate it with illegal downloading or watching Netflix in another country. But like Tor (which runs on VPNs), a VPN is an important privacy tool. Short for Virtual Private Network, a VPN can redirect your internet traffic to another server in another country, thereby concealing your actual geographical location.
There are countless VPN services available today, all with varying degrees of quality and cost. But in my experience, the best two are ProtonVPN (my current service and owned by Protonmail) and Tunnelbear. But try to avoid free VPN services – if you’re not paying for the product, you are the product.
Carefully consider what smart home devices you should have

Edgar Cervantes / Android Authority
But Internet of Things (IoT) devices can have very lax privacy policies and bad security features, and this can let bad people into your private life. One example is security cameras linked via the internet. All it takes is for someone to hack through the firewall, and suddenly they can see inside your house. Baby monitors can be another risky thing to have.
I’m not saying to be completely paranoid about all this stuff. They can be extremely useful gadgets and make life extremely convenient and comfortable. Just show good judgment and think about the possible downsides of introducing all these things into your home. Be selective in what you install and exercise good security practices.
Install a malware detection tool and firewall
I’ve heard it often said these days that malware detection tools and firewalls are no longer needed. That the internet “has moved on.” Yet these are the same people who end up with hacked Facebook accounts and click on email links. The sad fact is that malware has gone nowhere and intends to go nowhere. It has always been around. So it would be highly irresponsible not to have some protection.
Granted, Windows does have a built-in firewall and a malware tool called Microsoft Defender. But it isn’t the best out there, and there are definitely better alternatives for Windows PCs. On the Apple side, malware is less common (don’t attack me, Apple haters), but you can still get all the big-name companies offering Mac versions of their products. It’s better to be safe than sorry. There are also malware detection tools for iPhone and Android.
Install all security patches for Windows and Mac computers
Palash Volvoikar / Android Authority
If you use a Windows PC or a Mac (more a Windows PC than a Mac), you may get really irritated at the constant demands to update your PC with the latest patches. But you should remember that the more your computer gets patched, the more secure it will be.
Password-protect your home Wi-Fi network
Ankit Banerjee / Android Authority
Having an open Wi-Fi network (one that isn’t password-protected) is a really bad idea. Not only will you have neighbors and strangers leeching off your connection, but anyone can use your internet to download anything illegal. Whether that’s music, movies, or, God forbid, pornography, that will be on you if the police come knocking at the door. Failure to add a password to your Wi-Fi network is not a viable defense in court.

If there is no password on your router, go to the router page immediately and add one. Usual password rules apply. No pet names, squirrel noises, tribal oaths, or birthdays.
Make backups of everything on your computer and phone

This is another thing that we constantly preach here at Android Authority Death Star HQ. Back up everything. Make a backup of the backup of the backup. Automate that backup. Encrypt that automated backup. Be obsessed with backups.
Make your phone passcode longer and more complex
Phone passcodes are usually four digits by default. While this makes remembering them and typing them in very convenient, it doesn’t take long for someone to brute-force their way in. However, if you extend that PIN code to six digits, it suddenly becomes much more difficult and longer to break in. Extend it even further to nine digits, and short of a supercomputer, nobody has a chance of getting into your device.
On an iPhone, you can change your passcode by:
- Go to Settings > Face ID & Passcode.
- Tap Change Passcode.
- Once you enter your old passcode, tap Passcode Options.
- Choose either Custom Numeric Code (all numbers) or Custom Alphanumeric Code (letters and numbers.)
On an Android phone, you can change the passcode by:
- Go to Settings > Security > Screen Lock (the wording may vary depending on your Android model.)
- Enter your old PIN.
- Choose the style of the new PIN and enter it.
Encrypt your computer
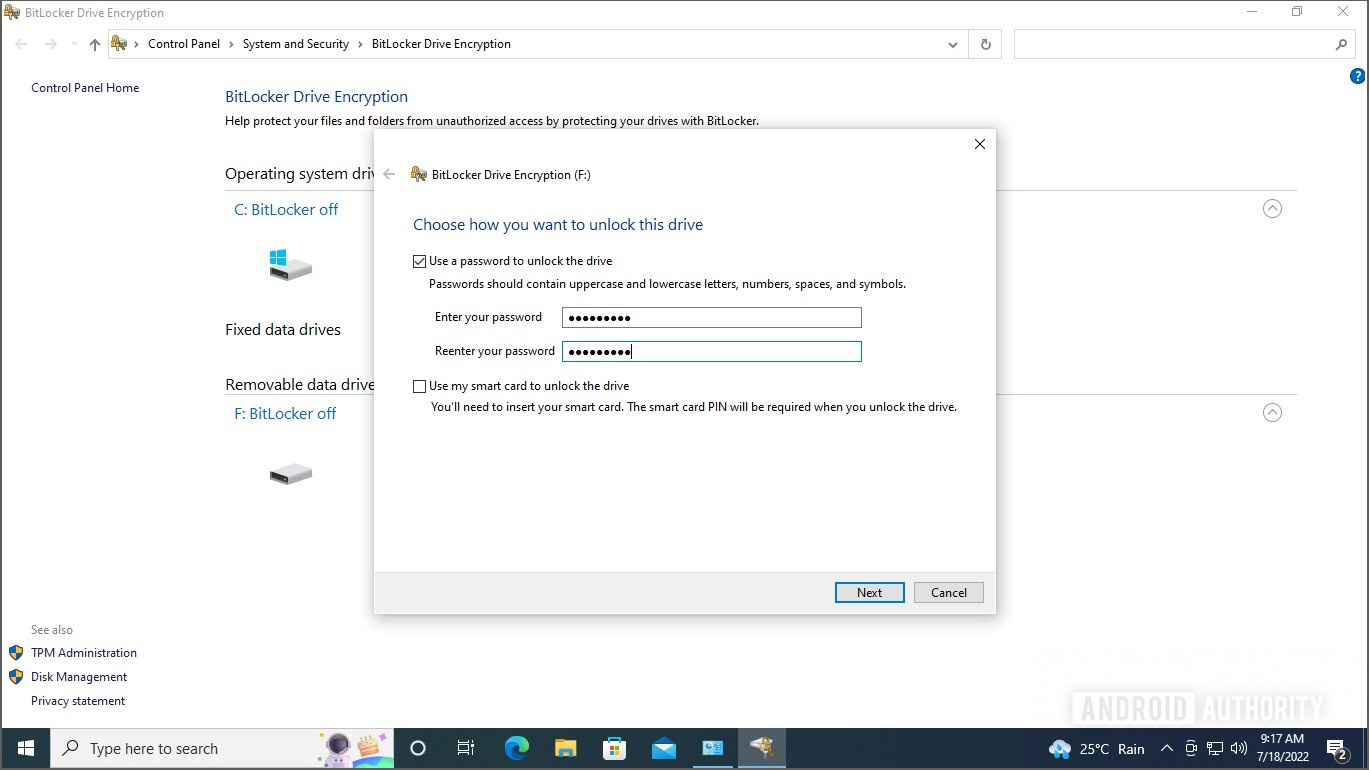
Encrypting your computer has become so much easier over the past years. Windows gives Bitlocker to anyone with a professional version of Windows, and Mac computers have built-in encryption with FileVault.
Be careful with certain file types
Be extra careful with files that have the format EXE, ZIP, RAR, ISO, or anything which is an operating system script. If in doubt, don’t open them.
But saying that, other file formats are not immune. It is possible, for example, to hide a virus or a hidden script inside a JPG image file.
Run any downloaded suspicious files through VirusTotal
If you absolutely have to download a file, run it through VirusTotal first. This scans files online without having to download them first, using multiple anti-virus services. It also checks URLs. You can upload already downloaded files, scan undownloaded ones by providing the URL, or email a suspicious file.
The process is made even simpler by the use of browser extensions, so you can just right-click on the file link.
Give an identity password to companies you’re a customer with

Tell your cable company, phone company, and internet provider not to talk to anyone about your account without providing a password first. Social engineering is becoming more common, which is when someone calls up pretending to be you to gain details about your account.
So put a password or PIN on your account to stop this from happening. Most big companies already have this feature, but some require you to opt in by requesting it.
Be careful what you post on social media

Joe Hindy / Android Authority
Social media is where all the cool kids hang out, and of course, companies rely on making money with Facebook, Instagram, TikTok, and others. So there are definite advantages to using social media. It’s also fun to connect with your friends. But of course, we come back again to revealing too much of ourselves, which can lead to identity theft.
Again, it all comes down to common sense and judgment, but the main highlights would be:
- Don’t allow anyone to tag you in photos.
- Keep all personal stuff to Friends Only.
- Keep your phone number off social media and deny all requests to upload your contacts.
- Don’t check in at various locations.
- Don’t post photos of your child or other children.
Use fake answers for security questions
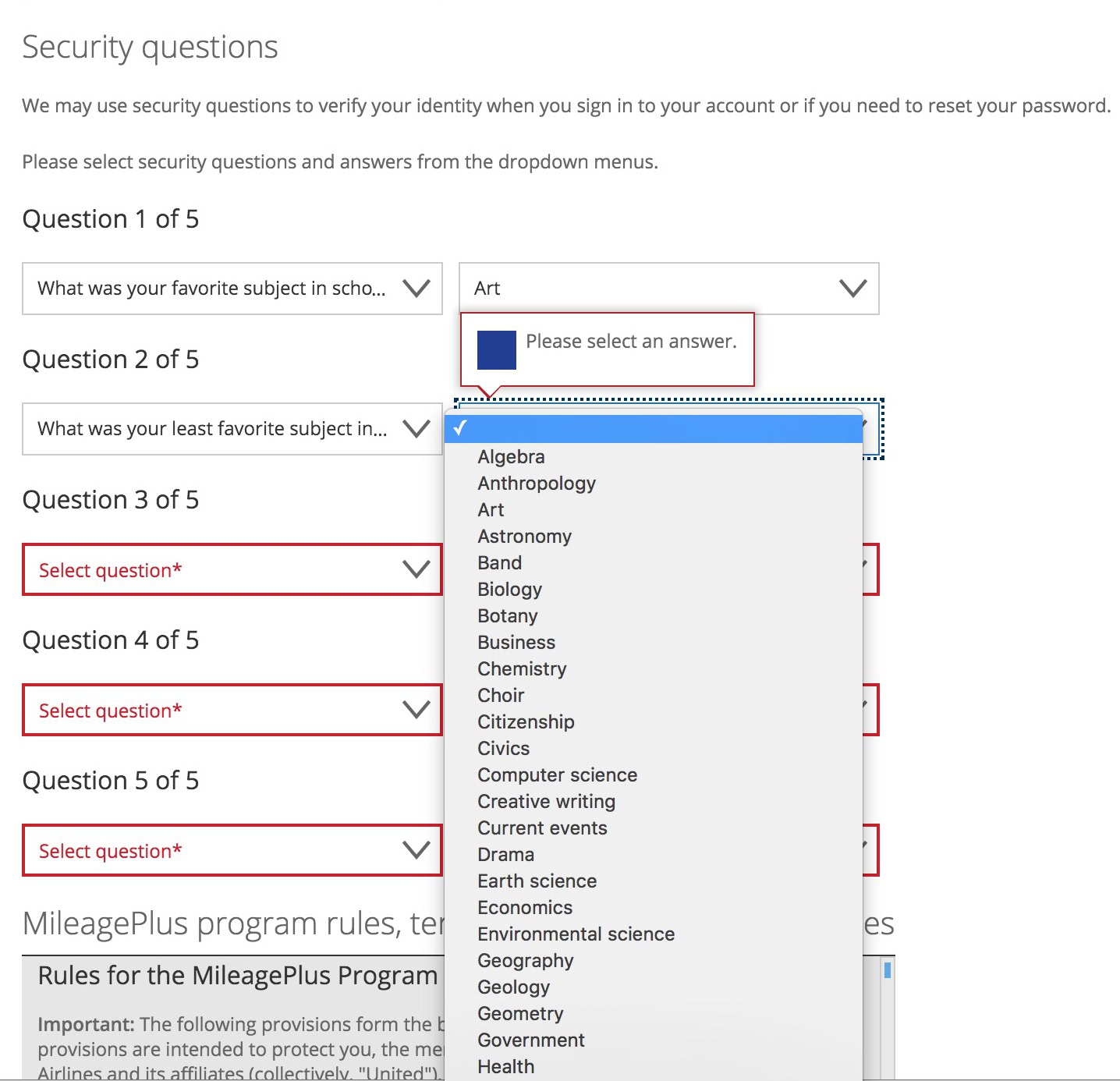
I covered this in my article on making a strong password. When making replies to security questions, many people tell the truth. So anyone with knowledge of that person is likely going to know the answer. So instead, make up silly replies that nobody will ever guess.
- Where were you born? In a hospital.
- Where did you first live? In a house on a street.
- Who was your first teacher? Some old lady with bad breath.
- Where did you go on your first date? Paradise.
- What was your first car? One with four wheels and doors.
- What was your first job? Earning money.
- What time of the day were you born? I wasn’t looking at a clock. I was a bit busy.
- What’s your grandmother’s first name? Granny.
Cover your computer webcam

Kris Carlon / Android Authority
You’d be hard-pressed to find a computer these days without a built-in webcam. They’re so small and unobtrusive that they can be easy to overlook. But if anyone can gain access to that webcam, they can literally look right at you. They can record you, listen to you, see your surroundings, and more. Sci-fi paranoia? Not quite.
The easiest solution is to put a piece of tape over the webcam. But you can also buy proper webcam covers which you can slide back and forth. Highly recommended.
Don’t click on short links
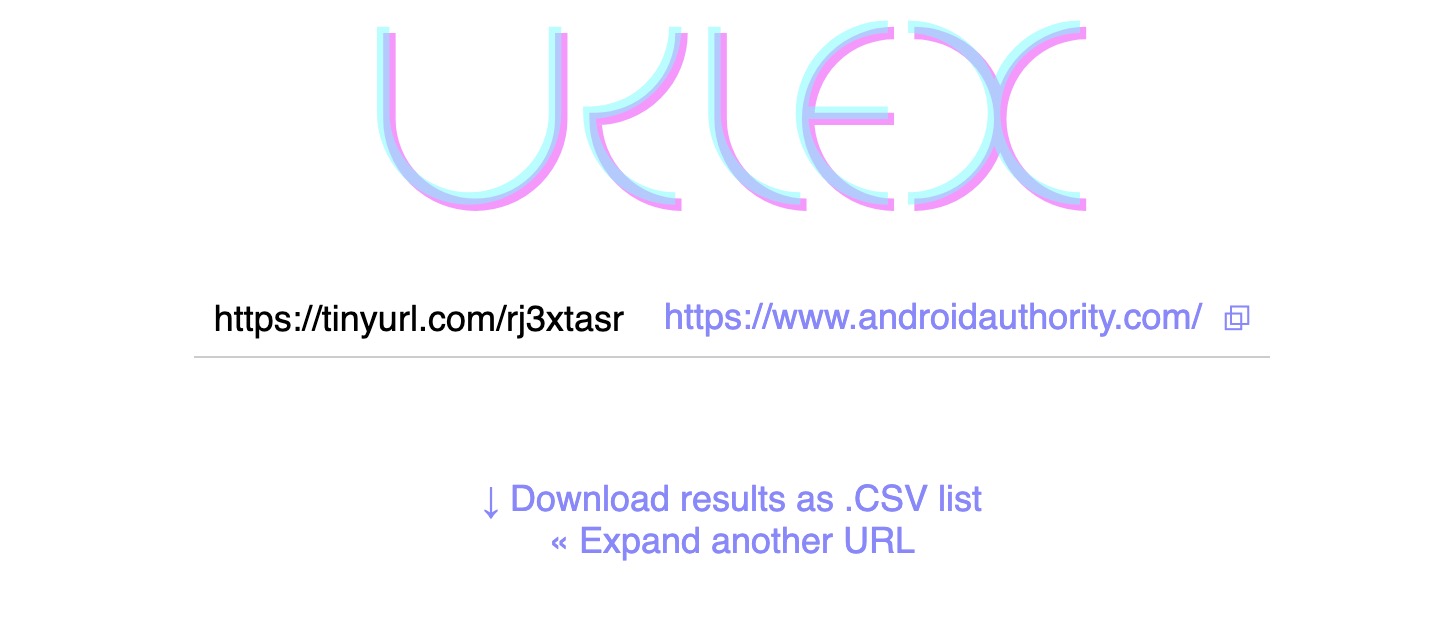
Short links are designed to make links more attractive to click. Companies also use them as a marketing tool. The New York Times, for example, uses the nyti.ms domain for short links. But the problem with short links is that, for the vast majority of them, you have no idea where they will lead to. A New York Times link can obviously be trusted, but what about a tinyurl.com link? A Bitly link? These can lead anywhere, such as an infected website or malware-infected file.
Try to avoid short links altogether, but if you must click one, run it through Text Expander first. It will reveal the link’s destination, and you can then decide if it looks legit or not.
Shut down all inactive and unneeded online accounts
I’m sure you all have ten Gmail accounts, various Twitter accounts, and maybe a couple of Reddit accounts. But do you really need them all? If any of those accounts are caught in a data breach, your personal information is exposed. So if you don’t need an account anymore, delete it.
Just go to the account settings and look for the account deletion option. Some accounts will be made inactive for 30 days in case you change your mind, but others are shut down immediately. The fewer accounts you have floating around out there, the better.
Log out from devices and accounts when you’re not using them
Adam Birney / Android Authority
If you use a computer that is shared by others (family, friends, colleagues, acquaintances), then the opportunity is there for them to snoop on your account. So when you are finished checking your email or social media, log out.
FAQs
The common consensus is that it is not worth it anymore. Even the inventor of PGP has given up on it, saying it has become too complicated for the average user to use.
Metadata is any identifying data on a file. Image metadata can be the name of the camera that took the photo. Email metadata could be when the email was sent.
It is an encrypted connection between your computer and the server upon which the website you’re visiting sits on. A secure connection stops information from being intercepted while in transit between you and the website (and vice-versa).
A VPN redirects your internet activity to a server either in your country or another country. This makes it impossible for anyone to eavesdrop on what you’re doing or to trace you back to your actual location.
No company is going to admit to it, and if they are, it would certainly take a lot of computer processing power to listen 24/7. Although Facebook is suspected of it, the consensus is that they are not.
For all the latest Technology News Click Here
For the latest news and updates, follow us on Google News.
