GitHub offers secret scanning for free
Open source software development service has made it easier for developers using its public repositories to keep coding secrets and tokens close to the chest.
Microsoft’s Git-based open source Internet hosting service for software developers is expanding its secret scanning partner program. Hitherto, this service was available only to GitHub Advanced Security users. With this advance, it will be open to all public repositories for free.
The program, scanning repositories for over 200 token formats, allows developers to track any publicly exposed secrets in their public GitHub repository. This year, with over 94 million developers across its repositories, the program found over 1.7 million potential secrets exposed.
SEE: Hiring kit: Python developer (TechRepublic Premium)
In a blog, Github product managers Mariam Sulakian and Zain Malik wrote that exposed secrets and credentials, the most common cause of data breaches, have a dwell time of 327 days on average before they are identified.
“These data beaches have shown that credential leaks can lead to severe consequences,” they wrote. “Still, organizations struggle to detect leaks at scale and take prompt action to fix any exposed secrets.”
Secret scanning free on all public repos
Currently GitHub partners with service providers to flag leaked credentials on all public repos through its secret scanning partner program. The new release gives open source developers free access to the alerts about leaked secrets in code — enabling them to identify the leak’s source, easily track alerts and take action (Figure A).
Figure A
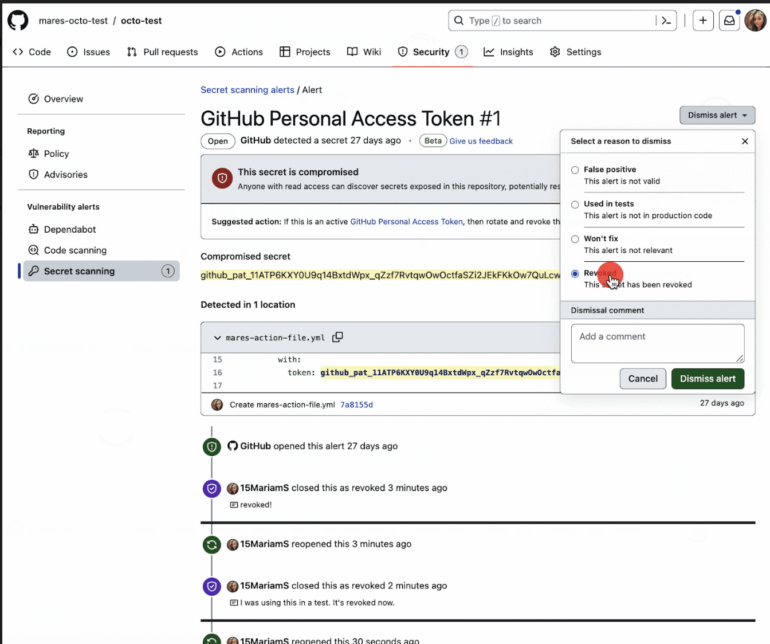
GitHub launched the secret scanning for public repositories as a beta this month. Users have to activate it within the platform’s security settings, but the rollout of the service is going to be progressive with full availability to all users by the end of January 2023.
Push protection for custom patterns
GitHub introduced push protection to GitHub Advanced Security customers in April 2022 to proactively prevent leaks by scanning for secrets before they are committed. Since then, Sulakian and Malik wrote again, the feature has prevented more than 8,000 secret leaks across 100 secret types (Figure B).
Figure B
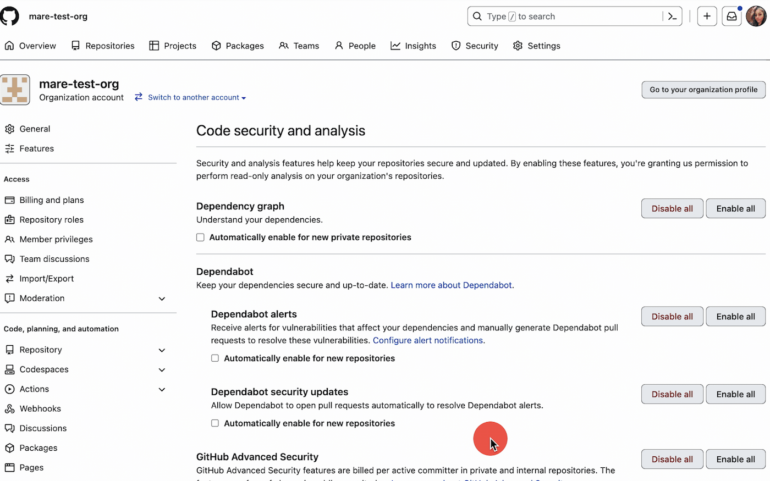
Now, wrote the product managers, organizations that have defined custom patterns can enable push protection for those patterns. They explained that push protection for custom patterns can be configured on a pattern-by-pattern basis.
“Just like how you can already choose which patterns to publish (and which to first refine in draft mode), you can decide which patterns to push protect, based on false positives,” they said.
SEE: Open source code for commercial software applications is ubiquitous, but so is the risk (TechRepublic)
With the new feature, organizations with GitHub Advanced Security have additional coverage for what are often their most important secret patterns — the ones customized and defined internally to their organizations.
The new program lets service providers partner with GitHub to have their secret token formats secured through scanning, which searches for accidental commits of secret formats. It can then be sent to a service provider’s verify endpoint.
How secrets and tokens work in GitHub
In GitHub, “secrets” allow developers to authenticate their workflow run. When a developer starts a GitHub Project, GitHub automatically creates a unique GITHUB_TOKEN “secret,” which allows the developer access to GitHub Apps that are installed on the dev’s repository. The GITHUB_TOKEN expires when a job finishes or after a maximum of 24 hours. If a GitHub project communicates with an external service, the owner might use a token or private key for authentication.
Both tokens and private keys are secrets that a service provider can issue. If a user checks a secret into a repository, anyone who has read access to the repository can use the secret to access the external service with the user’s privileges. GitHub recommends that users store secrets in a dedicated, secure location outside of the repository for their project.
Interested in taking the next step toward coding comprehension for game development? Check out The Ultimate Learn to Code Training.
For all the latest Technology News Click Here
For the latest news and updates, follow us on Google News.
