Researchers just outlined a new vulnerability that affects processor chips — and it’s called Hertzbleed. If used to conduct a cybersecurity attack, this vulnerability can help the attacker steal secret cryptographic keys.
The scale of the vulnerability is somewhat staggering: According to the researchers, most Intel and AMD CPUs might be impacted. Should we be worried about Hertzbleed?
The new vulnerability was first discovered and described by a team of researchers from Intel as part of its internal investigations. Later on, independent researchers from UIUC, UW, and UT Austin also contacted Intel with similar findings. According to their findings, Hertzbleed might affect most CPUs. The two processor giants, Intel and AMD, have both acknowledged the vulnerability, with Intel confirming that it affects all of its CPUs.
Intel has issued a security advisory that provides guidance to cryptographic developers on how to strengthen their software and libraries against Hertzbleed. So far, AMD hasn’t released anything similar.
What exactly is Hertzbleed and what does it do?
Hertzbleed is a chip vulnerability that allows for side-channel attacks. These attacks can then be used to steal data from your computer. This is done through the tracking of the processor’s power and boost mechanisms and observing the power signature of a cryptographic workload, such as cryptographic keys. The term “cryptographic keys” refers to a piece of information, securely stored in a file, which can only be encoded and decoded through a cryptographic algorithm.
In short, Hertzbleed is capable of stealing secure data that normally remains encrypted. Through observing the power information generated by your CPU, the attacker can convert that information to timing data, which opens the door for them to steal crypto keys. What’s perhaps more worrying is that Hertzbleed doesn’t require physical access — it can be exploited remotely.
It’s quite likely that modern processors from other vendors are also exposed to this vulnerability, because as outlined by the researchers, Hertzbleed tracks the power algorithms behind the Dynamic Voltage Frequency Scaling (DVFS) technique. DVFS is used in most modern processors, and thus, other manufacturers such as ARM are likely affected. Although the research team notified them of Hertzbleed, they are yet to confirm whether their chips are exposed.
Putting all of the above together certainly paints a worrying picture, because Hertzbleed affects such a large number of users and so far, there is no quick fix to be safe from it. However, Intel is here to put your mind at ease on this account — it’s highly unlikely that you will be the victim of Hertzbleed, even though you are likely exposed to it.
According to Intel, it takes anywhere between several hours to several days to steal a cryptographic key. If someone would still want to try, they might not even be able to, because it requires advanced high-resolution power monitoring capabilities that are difficult to replicate outside of a lab environment. Most hackers wouldn’t bother with Hertzbleed when plenty of other vulnerabilities are discovered so frequently.
How to make sure Hertzbleed won’t affect you?
As mentioned above, you are probably secure even without doing anything in particular. If Hertzbleed gets exploited, it’s unlikely that regular users will be affected. However, if you want to play it extra safe, there are a couple of steps you can take — but they come at a severe performance price.
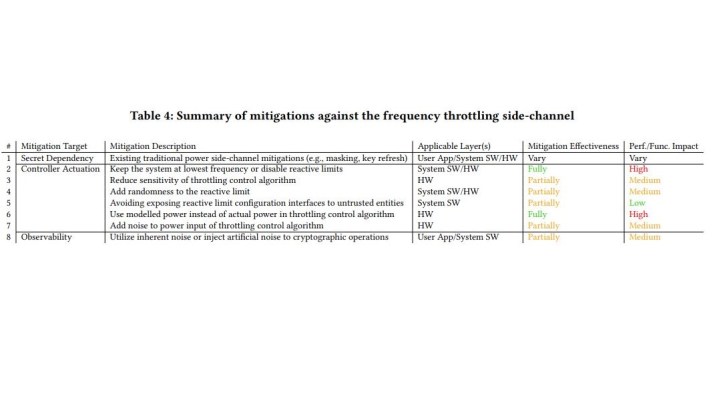
Intel has detailed a number of mitigation methods to be used against Hertzbleed. The company doesn’t seem to be planning to deploy any firmware updates, and the same can be said about AMD. As per Intel’s guidelines, two ways exist to be fully protected from Hertzbleed, and one of them is super easy to do — you just have to disable Turbo Boost on Intel processors and Precision Boost on AMD CPUs. In both cases, this will require a trip to the BIOS and disabling boost mode. Unfortunately, this is really bad for your processor’s performance.
The other methods listed by Intel will either only result in partial protection or are very difficult, if not impossible, for regular users to apply. If you don’t want to tweak the BIOS for this and sacrifice your CPU’s performance, you most likely don’t have to. However, keep your eyes open and stay sharp — cybersecurity attacks take place all the time, so it’s always good to be extra careful. If you’re tech-savvy, check out the full paper on Hertzbleed, first spotted by Tom’s Hardware.
Editors’ Recommendations
For all the latest Technology News Click Here
For the latest news and updates, follow us on Google News.