How the initial access broker market leads to ransomware attacks | ZDNet
To perform a ransomware attack successfully, cybercriminals must first obtain access to their victim’s PC or network.
Gone are the days when ransomware was confined to malware that targeted individuals with fake threats from organizations like the FBI or IRS, demanding payment through a PC pop-up following encryption.
Now, while individuals may still encounter ransomware — especially when antivirus programs are not in use — companies are the big game that criminals hunt.
Time is money in the corporate world, and ransomware has exploded in recent years to become an almost separate cybercriminal business of its own. As a result, ‘sub’ services have emerged that assist ransomware developers in the deployment of their illicit creations — ranging from language services to handle ransom payment negotiation to Initial Access Brokers (IABs) who offer the covert access to a network required in the first stage of a ransomware attack.
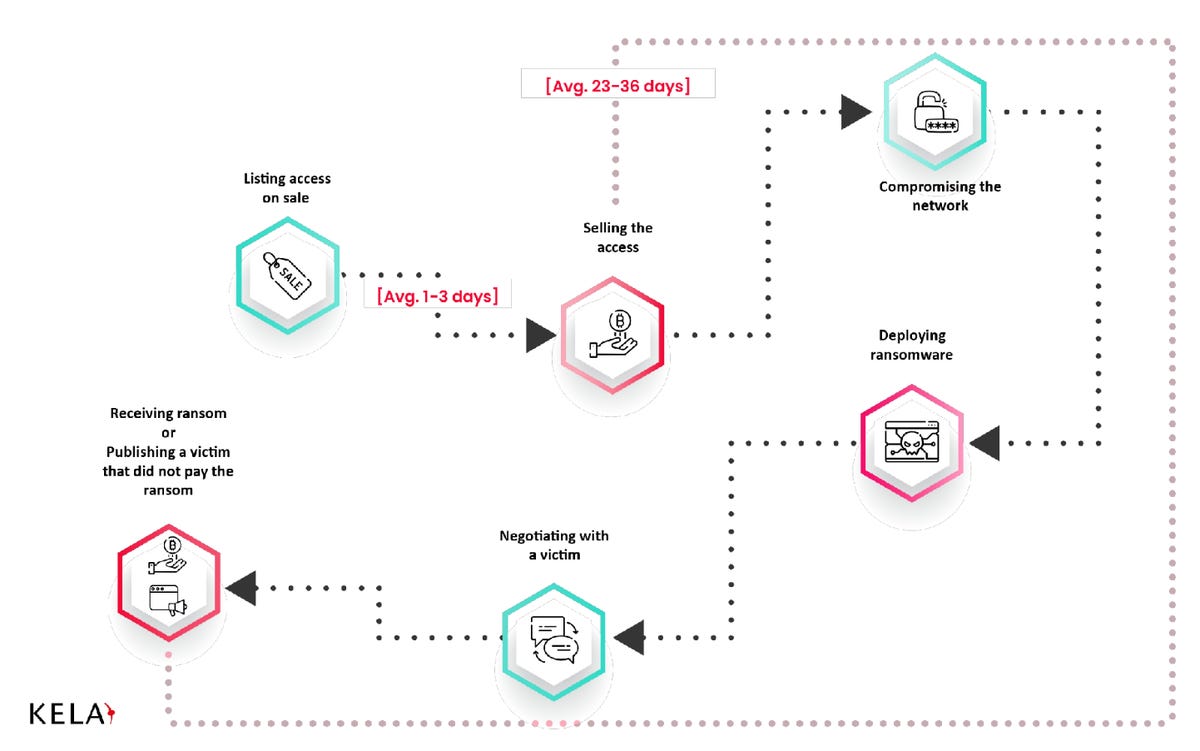
As noted in new research conducted by KELA, the ransomware-as-a-service (RaaS) economy relies on IABs to reduce the need for extended reconnaissance or the time to find a method for entry.
On average, IABs sell initial access for $4600, and sales take between one and three days to finalize. In the cases identified by the cybersecurity firm, once access has been purchased, it takes up to a month for a ransomware attack to take place — and potentially for the victim to be subsequently named and shamed on a leak site.
KELA
At the very least, five known Russian-speaking ransomware operators are using IABs: LockBit, Avaddon, DarkSide, Conti, and BlackByte.
KELA conducted an examination of past security incidents involving these ransomware groups. First up is LockBit, of which an attack began against Bangkok Airways due to AnyConnect VPN access offered by a threat actor called “babam.”
While it isn’t clear exactly who purchased Bangkok Airways access, on August 23, 2021 — not yet a month after access was offered in underground forums — the airline became infected by ransomware. Two days later, Bangkok Airways appeared on the LockBit leak site.
“Bangkok Airways did not disclose any investigation details, but based on the timeline, it is highly possible that the attack was performed using the bought access,” the researchers noted.
KELA
In an attack conducted by Avaddon, access to a UAE steel product supplier was found to be up for sale on a forum in a post dated March 8, 2021. Three weeks later, the company appeared on the Avaddon domain. (This group has reportedly closed down and a tool has been made available to generate decryption keys.)
DarkSide is infamous for an attack on Colonial Pipeline that caused fuel panic-buying in the United States. However, in a separate incident taking place on January 16, 2021, the same “babam” IAB tried to sell access to mining technology firm Gyrodata.
Two days later, access was declared as sold, and between January 16 and February 22, an unauthorized actor was lurking on the firm’s networks. On February 20, DarkSide published the company’s name as a victim.
In another case, access to a US manufacturer was sold on October 8, 2021, for $800. Within two weeks, Conti exposed the firm on its leak site and some stolen data was also published online.
Ransomware attacks against high-profile targets won’t be going away anytime soon. Just before the Super Bowl kicked off, the San Francisco 49ers became the latest victim of BlackByte, who also named the organization on a leak website.
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
For all the latest Technology News Click Here
For the latest news and updates, follow us on Google News.
