Microsoft Defender 365: Automation to fight automated attacks
When you think about everything in your organization that you need to defend from attackers, it’s easy to come up with a list of servers, PCs, file stores, users and more that could be affected, but attackers think of those as a graph of resources that are all connected. Compromising one of them leads to other parts of your infrastructure. Increasingly, attackers move across your connected tools with automated toolkits, scripts and cloud resources.
Now, security teams can do the same, because Microsoft 365 Defender builds a picture of how an attack affects your system and uses that to try and shut it down — automatically and in real time.
Jump to:
Defender automatically disrupts attacks
Rather than leaving intervention to the security admins, Microsoft 365 Defender will try to automatically disrupt the attacks it detects. It aims to contain attacks while they’re in progress, using AI to look at signals and isolate assets that have already been affected.
That might mean suspending a compromised user whose account is being used by an attacker, resetting their password to limit access, blocking URLs in email, removing messages and putting attachments in quarantine, automatically isolating infected devices or offboarding them completely.
Isolating the suspicious device disconnects it from everything except the connection to the Defender service — so that you can use the connection for automated cleanup afterwards or to reconnect the device if it turns out to be a false positive (Figure A).
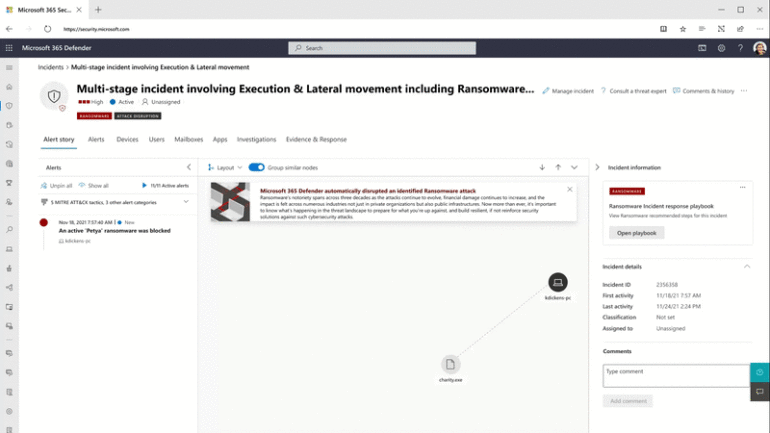
A flood of attacks mean less contextual defense
It can take under two hours from the time an employee is tricked into clicking on a phishing link to the attacker getting full access to their inbox. From there, the attacker can set forwarding rules to send emails asking for money or confidential information that look as if they come from a legitimate employee.
The attacker then moves on to attack other internal systems. It can take only minutes for a ransomware operator to encrypt hundreds of devices.
Defenders are never going to keep up with that by manually responding to the flood of alerts. Most organizations won’t even know they’ve been breached until much later. Even if you do catch an alert from your security tools about suspicious behavior, can you be sure that you’ve noticed every attack and blocked every vulnerable surface, given how siloed many security tools are?
“A lot of the time, we’re basically playing Whack a Mole with the attacker,” said Raviv Tamir, vice president of Microsoft 365 Defender. “I’m sitting on an endpoint, I see something suspicious, I whack it with my hammer and I try to stop it. Say I did, and then I see something else on another endpoint and I whack it. Then I see something else. Even if we stopped all these things, does it mean that we stopped the attack? The answer is that we don’t know, because we’re playing at the level of bricks and they have the whole Lego set.”
SEE: Mobile device security policy (TechRepublic Premium)
Defender goes beyond XDR capabilities
The idea behind extended detection and response was to take the multiple security tools and other sources of information and have them not just share information but know which source of information is authoritative. The antimalware software protecting a laptop might detect that the device has been compromised, and that should be more significant than the identity service saying everything is fine with the account on that laptop.
“Rather than just chat with each other, the security tools need to have a source of truth they all look at,” Tamir said.
Defender now has central sources of truth for the state of devices, identities, files and URLs that its machine learning models can use to correlate alerts and suspicious events into an incident that corresponds to an entire attack as it occurs.
“Now I can start asking the really tough question: Where did it come from?” Tamir asked. “What was the root cause? Is it some misconfiguration? Is it a vulnerability? Is it the user being socially engineered to do something? Did we stop it? Did we intervene? More importantly, did I succeed at stopping it — or did it progress after I intervened and I’m still just playing Whack a Mole? This is the really exciting level of the game, because now we’re really playing at the same level as the attackers.”
Defender’s capabilities let you understand and react to the attack itself, not just the individual results of that attack on different resources.
Defense of all endpoints: Even unmanaged ones
Because not all devices are managed directly by Defender, you can’t rely on Defender being able to lock them down directly if they’re compromised.
“Obviously I can control all the endpoints where the sensor was turned on,” Tamir said. “If you deploy Microsoft Defender for Endpoint, I have control. What about endpoints where you didn’t? Maybe it’s a BYOD device or an enterprise IoT device. Maybe it’s a device that just wasn’t onboarded and is sitting on the network. Clearly, the attacker is going to go for that device.”
Defender also attempts to contain a compromised device using a technique he calls reverse isolation.
“We have isolation capabilities on the firewall,” Tamir said. “Basically, we’re telling all our devices not to communicate with that device. We just don’t trust that thing: Please don’t accept any requests from it and don’t communicate back to any of its requests. Shut it out of the network.”
As well as disrupting attacks, Defender will try to undo any damage, with a feature Microsoft calls self healing.
“If I managed to intervene and stop the attack: can I reverse the bad things that have happened?” Tamir asked. “If I think a machine is compromised, can I help it get back to a working state? How many of these artifacts that are potentially going bad like files that are malicious, changes that happened in the registry — how many of those can I revert?”
Business email compromise attacks often involve creating email forwarding rules that allow the attacker to reply on behalf of the user and ask for money to be transferred to them.
Avoiding false positives
While automation is a powerful tool, getting it wrong could be as disruptive as an actual attack, so Microsoft is rolling this out cautiously.
“We need to be careful where we run it, because it’s awesome when we run disruption and stop human operated ransomware from encrypting all your devices,” Tamir noted. “If I’m right and I’m stopping ransomware, everyone is going to applaud because I just saved that enterprise a lot of money. However, if I made a mistake, and I’m isolating these machines because I think it’s ransomware but it isn’t, then I’ve just disrupted operations significantly.”
Key systems are out of bounds for Defender’s automatic disruption for exactly this reason. Because of that, automatic attack disruption currently works for just two scenarios that Microsoft views as the most important to stop:
- Business email compromise campaigns.
- Human-operated ransomware attacks.
Both attacks do significant damage because they affect a wide range of resources and individuals. They require an end-to-end view but can be disrupted across the organization.
Defending more devices
Disruption depends on Microsoft 365 Defender getting enough signals, so it will be more effective if you use multiple Defender products.
“The more sensors we get, the better we are at finding out what’s happening,” Tamir said. “The more products you have, the better hammers that we have. The more of our products you deploy, the more visibility you get, the more tools we get to try to whack the thing, and our disruption will get better.”
Network isolation is now available for Linux devices running Defender for Endpoint, although it can’t do the full device containment. The feature is in public preview, so expect it to develop over time.
“Linux isolation is another hammer for me to use,” Tamir said. “If that attack crosses a Linux device, I have a way to try to influence it.”
In the long run, he’s hoping to get parity across multiple operating systems.
“I want to get the same tool sets across everything so my automation can try to disrupt attacks everywhere,” he continued.
Tamir also wants to extend the places where Defender can automatically defend against attacks beyond what you might usually think of as a security system. That includes working with the Windows kernel team to get more information than was in device logs, and it also includes working with the Azure AD team to automatically manage device access.
“I want control not just on the endpoint, but on the endpoint firewall,” Tamir said. “I want control on the identity system: I want direct control on conditional access, and Azure AD is actually giving us that. I want to have the same things in Active Directory even if the customer doesn’t have Azure AD. I want to control basically any entity that I can, and my dream is that one day, I can use our SIEM solution, Sentinel, to also extend it to other products that are not Microsoft products.”
Tamir also wants to tackle one of the underlying problems: How complex and time consuming it is to manually configure devices and services correctly.
“Configuration needs to go through a big overhaul,” he said. “The fact that everything’s manual is horrible. It should stop, and I’m working to fix it.”
For all the latest Technology News Click Here
For the latest news and updates, follow us on Google News.

