New cybersecurity BEC attack mimics vendors
Financial supply chain compromises, a subcategory of BECs, appear to be ascendant and highly effective. Abnormal Security has identified one pernicious threat actor that it has dubbed Firebrick Ostrich, which is using a subtype of these gambits to trick targets into making payments.
The firm previously identified four kinds of financial supply chain compromise, which dispense with impersonation of internal executives at the target company and instead wear the garb of one of the company’s vendors. Abnormal Security says Firebrick Ostrich has used one of these types of financial supply chain compromises — third-party reconnaissance attacks — to commit 346 BEC campaigns dating back to April 2021, impersonating 151 organizations and using 212 maliciously registered domains, nearly all in the U.S.
Crane Hassold, director of threat intelligence at Abnormal Security, said the amount of money that can be gotten from external, third-party impersonation is three times higher than traditional BEC exploits, and that their success stems from awareness deficit, as companies and their employees are trained to look for emails impersonating an internal executive, not a vendor.
“Also, when you look at third-party reconnaissance and other financial supply chain attacks, the effectiveness of the lure is in the amount of information they are able to put in emails — information that makes them look a lot more realistic than other forms of BEC,” he said.
SEE: Mobile device security policy (TechRepublic Premium)
Hassold noted that tens of billions of dollars have been lost due to BECs in any given year, and that BECs are a leading cause of financial loss at enterprises going back to 2016.
“BECs really exploded and peaked in the first six months last year, driven by attackers impersonating external entities, a big change because, since its inception, BECs have primarily involved impersonating internal entities,” he said. “BEC actors have identified third parties — including vendors — as a weak link in the chain.”
Jump to:
Big gains from low-tech impersonation
From the perspective of cybercrime as a business, the overhead needed to launch third-party reconnaissance attacks is low, according to Hassold; it requires basic reconnaissance and information gathering, without underlying infrastructure or developers to maintain and enhance malware. “It’s just sending out emails, so from the overhead perspective it’s fantastically lucrative,” he said.
Third-party impersonation exploits, most of which originate from West Africa, per Abnormal, use a three-step process (Figure A).
Figure A
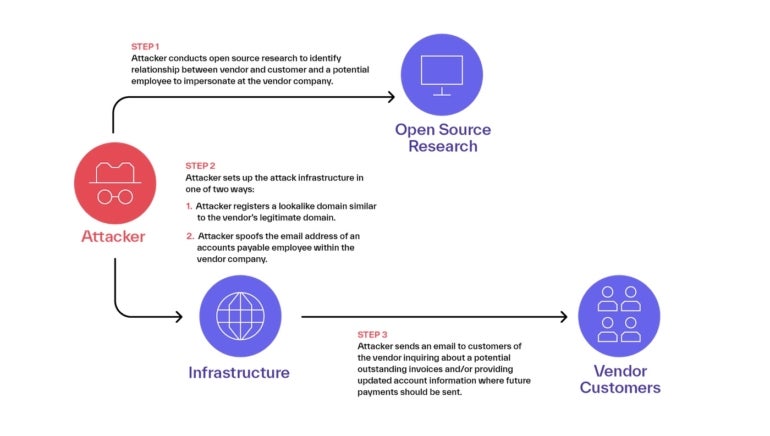
- Open-source research on vendor customer relationships, which could come from state and local governments that offer detailed information about existing and previous contracts, or a vendor’s website where the company has displayed the names or logos of their customers, or even googling company names to see possible connections.
- Attack infrastructure: The group registers a domain, using Namecheap or Google as registrar that impersonates the vendor domain, and spoofs the email addresses of accounts payable employees within the vendor company.
- Targeted email to customers: The attacker sends an email to customers of the vendor inquiring about potential outstanding invoices or providing updated account information where future payments should be sent.
Attacking within a week of registering the domain name
According to Abnormal Security, Firebrick Ostrich’s use of newly-registered domains highlights how young domains, in conjunction with other behavioral indicators, can be used as an effective signal to identify threats. Abnormal Security reported that 60% of the domains registered by Firebrick Ostrich were registered on the same day as the execution of the BEC campaign in which they are deployed; approximately three quarters of their domains were obtained within 48 hours of an attack, and 89% of their domains were registered within a week of a campaign.
SEE: Here’s how IT budgets should fill cybersecurity moats in 2023 (TechRepublic)
Using the newly-registered domains, Firebrick Ostrich creates email addresses impersonating actual vendor accounts staff that they then use to facilitate their attack, with the primary account communicating with a target by mimicking a vendor’s actual accounts receivable specialist. The supplemental email accounts, which can include financial executives at the vendor, add a layer of authenticity to their attacks, per the firm.
“Reasonable” requests and a long-game tactic
Abnormal Security’s report said the initial email in a Firebrick Ostrich attack typically starts with a greeting like the vendor “greatly appreciates you as a valued customer and we want to thank you for your continued business,” followed by two possible requests:
- The first request indicates the vendor would like to update the bank account on file with the customer. The email makes a point to mention that the vendor is unable to receive payments via check, so ACH and wire transfer payments are the only options available.
- The second request inquires about any outstanding payments that are owed to the vendor. The email states that the vendor has lost track of open invoices on their end because their accounting team is unable to review accounts. In one email, Firebrick Ostrich provided more details, stating that the account team is “not able to get onto the server or into Oracle to review accounts or post payments that may have been received.”
“The manufactured pretext of a technical issue is a common excuse used in many of the third-party reconnaissance attacks we see to explain why a vendor isn’t able to access their own inventory of invoices, but the flattery shown here seems to be unique to this BEC group,” said Hassold.
Another tactic is particularly stealthy because it does not request payment for a current invoice, but simply asks that a vendor’s stored bank account details be updated so any future payments get redirected to the new account. This sidesteps red flags that accounts payable specialists may have been trained to notice, according to Abnormal Security. The longer game is that the threat actors will get paid with the next invoice, instead of the actual vendor.
What makes this group fairly unique is that they have seen massive success even without the need to compromise accounts or do in-depth research on the vendor-customer relationship. By using fairly obvious social engineering tactics, they can discover everything they need in order to run a successful BEC campaign — without investing any significant time or resources into the initial research, per Abnormal Security.
The best defense is holistic screening
Hassold said that email-flagging technologies that identify static indicators won’t be sufficient to defend against BEC attacks; he recommended a more holistic defense using such techniques as behavioral analysis to understand the relationship between the sender and recipients. This holistic strategy would also incorporate information about the target company’s third-party vendor ecosystem and monitor both for specific impersonation attacks spoofing those vendors and suspicious language and artifacts.
“Understanding what trends are being seen in the overall cyberthreat landscape and making sure employees are aware of these are critical,” he said. “That means when they see a Firebrick Ostrich-type attack with requests for an account change or messages about technical difficulties, there’s already an internal policy in place to validate those requests offline with the vendor well before changes are actually made. We think of cyberattacks as very sophisticated things, but at the end of the day a vast majority are nothing more than social engineering, trying to manipulate human behavior — getting someone to do something they wouldn’t otherwise do.”
With cybersecurity attacks likely to rise this year, and threat actors becoming more sophisticated in their methods, this also might be a good time to put on the white hat. Learn the ropes for $30 with these nine ethical hacking courses offered through TechRepublic Academy.
For all the latest Technology News Click Here
For the latest news and updates, follow us on Google News.