What is Electronic Code Book (ECB) encryption and how does it work?
What is Electronic Code Book (ECB)?
Electronic Code Book (ECB) is a simple mode of operation with a block cipher that’s mostly used with symmetric key encryption. It is a straightforward way of processing a series of sequentially listed message blocks.
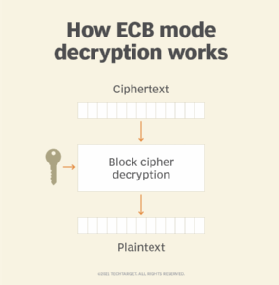
The input plaintext is broken into numerous blocks. The blocks are individually and independently encrypted (ciphertext) using the encryption key. As a result, each encrypted block can also be decrypted individually. ECB can support a separate encryption key for each block type.
In ECB, each block of plaintext has a defined corresponding ciphertext value, and vice versa. So, identical plaintexts with identical keys always encrypt to identical ciphertexts. This means that if plaintext blocks P1, P2 and so on are encrypted multiple times under the same key, the output ciphertext blocks will always be the same.
In other words, the same plaintext value will always result in the same ciphertext value. This also applies to plaintexts with partial identical portions. For instance, plaintexts containing identical headers of a letter and encrypted with the same key will have partially identical ciphertext portions.
For any given key, a codebook of ciphertexts can be created for all possible plaintext blocks. With the ECB mode, encryption entails only looking up the plaintext(s) and selecting the corresponding ciphertext(s). This operation is like assigning code words in a codebook. In fact, the term “code book” derives from the cryptographic codebooks used during the United States Civil War (1861-1865).
In terms of error correction, any bit errors in a ciphertext block will only affect decryption of that block. Chaining dependency is not an issue. Any reordering of the ciphertext blocks will only reorder the corresponding plaintext blocks. It won’t affect decryption.
Data Encryption Standard vs. Electronic Code Book
The Data Encryption Standard (DES), developed by IBM in the early 1970s, became an official Federal Information Processing Standard (FIPS) in 1977. DES can use five modes to encrypt data. ECB is one of them and is the original mode of DES.
Three other modes, Cipher Block Chaining (CBC), Cipher Feedback (CFB) and Output Feedback (OFB), were added to the FIPS Publication 81. A fifth mode, the Counter Mode was later added to the NIST Special Publication 800-38a. These modes differ in their design principles, such as block versus (emulated) stream, whether initialization vectors are used and whether encryption errors are likely to propagate to subsequent blocks.
Of the five DES modes, ECB is the simplest and weakest, because repeating plaintext generates repeating ciphertext. As a result, anyone can easily derive the secret keys to break the encryption and decrypt the ciphertext. ECB may also leave obvious plaintext patterns in the resulting ciphertext.
The letters ECB following a cipher like DES or AES — DES-ECB or AES-ECB — indicate the use of the ECB mode.
What are drawbacks of Electronic Code Book?
There are some drawbacks to using ECB, including:
- ECB uses simple substitution rather than an initialization vector or chaining. These qualities make it easy to implement. However, this is also its biggest drawback. Two identical blocks of plaintext result in two correspondingly identical blocks of ciphertext, making it cryptologically weak.
- ECB is not good to use with small block sizes — say, for blocks smaller than 40 bits — and identical encryption modes. In small block sizes some words and phrases may be reused often in the plaintext. This means that the ciphertext may carry (and betray) patterns from the same plaintext, and the same repetitive part-blocks of ciphertext can emerge. When the plaintext patterns are obvious, it creates opportunities for bad actors to guess the patterns and perpetrate a codebook attack.
- ECB security is weak but may be improved by adding random pad bits to each block. Larger blocks (64-bit or more) would likely contain enough unique characteristics (entropy) to make a codebook attack unlikely.
Electronic Code Book and internet security
ECB was originally designed to encrypt messages that never span more than a single block, such as to encrypt keys to distribute for other operations. However, using ECB on a message that’s longer than a single block results in the leak of a bit per block. This is because ECB allows bad actors to disguise when two plaintext blocks are the same or different.
One example of this issue is photograph encryption. Despite the encryption, the very nature of ECB allows the photograph’s outline to show through plainly.
This is not because the encryption itself has failed, but because it is used in a way that was not intended. Internet protocols using a mode of operation that was not originally designed to encrypt multiple blocks introduces security risks into the system.
For all the latest Technology News Click Here
For the latest news and updates, follow us on Google News.
